Executive summary
This report focuses on the initial dynamic and static analysis of this malware dropper. Part 2 will cover the unpacking and analysis of the clean file. The malware sample was received from a third-party malware repository, and the sample (Gaara.exe) acts as a loader, dropping another file(Gaara the Kazekage) which will self-replicate across directories. Anti-analysis and evasion techniques are present, including modifying values in the registry and preventing analysis by blocking particular tools. Additionally, there is evidence that this malware connects to external networks.
Table of Contents
Infection Chain
Technical Analysis
Detonation: Running with User or Admin Previledges
Conclusion
Infection Chain
Sample seems to be masquerading as a video game from a website call hxxp://narutogames.com. Victims could potentially visit the domain and get tricked into thinking this is only a PC game by downloading the game (gaara.exe) on their device. Here’s a high level breakdown on the infection from what’s been gathered as of writing this report:
Technical Analysis
Technical analysis began by first engaging in static analysis. PE Bear was used to get a brief overview on the file header information and also look at the imports. Attention can be drawn towards the HexDump on the left starting offset of 40 to A0 (The DOS Stub section, This Program cannot run in DOS). Seems like some type of XOR operation occuring possibly because of the pattern occuring (Part 2 of the analysis is better suited for this theory). As shown in this screenshot:

The IAT also tells us if there are any intresting imports being utzilized by the program. The lack of imports gives another indication that the sample is packed.
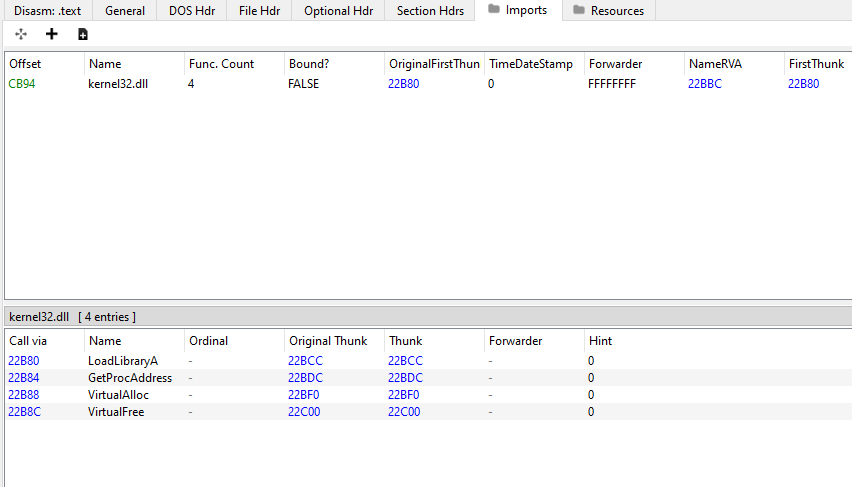
Detect-It-Easy will also display a visual graph showing the entropy in the different sections of the PE file. The entropy level and the Virtual Size and Raw Size size on disk (through PE View) both reaffirm that this sample is packed:
PE Bear
PE View
Through the strings analysis on X32 dbg, I typed some key strings that are common in malware (based off my past experiences) CPP, HTTP, W, Load,\, start, run, and registry. These strings would show if the language is based on C++ pontentially, outbound/inbound connections, any intresting file paths, start and run keys (to show persistance), and initial indictors of registry actions.
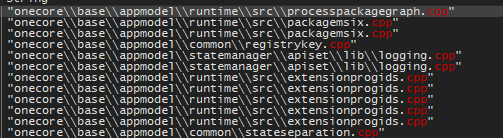
Instresting strings that could be part of the execution through a windows native service:
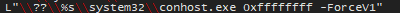
Associations with the boot up process of the machine. Could potential check on the status of its boot up to stage a persistance mechanisim:
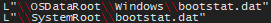
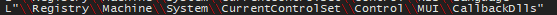
Registry actions referring to DLL communication:
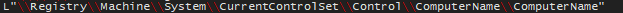

Crl.dll, also known as Common Runtime Language. Which is specefically used with C language:
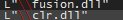
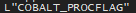
Found some suspicion that Cobalt Strike could be used because of this string. There are more indicators but this is just one (Part 2 of analysis addresses this):
Detonation: Running with User or Admin Previledges
Detonation was conducted in previledged mode and user mode. It’s to highlight the difference actions that occur when ran in with these roles.
User Previledges
The tools staged during detonation were Process Hacker and Procmon.I input gaara.exe in the search field on Process Hacker and added a Process Name filter on Procmon just to easily idenitfy and child processes or actions that occur with it running. After detontating the malware, gaara.exe dropped a file called Gaara The Kazekage on the desktop as shown on the image:
In order to control the amount of results from Procmon, filters were added to the RegCreateKey and RegQueryKey for Process Name and then added a filter for the highlight feautrure. Another filter added was the Operation is RegCreateKey to focus on this specefic operation while being able to quicly parse through the other filters that were in. This intresting file path for the RegCreateKey HKCRVBSFileShellOpen2Command and this other key showing persistance in the HKLMSoftwareWOW6432NodeMicrosoftWindowsCurrentVersionRun. Along with this other intresting keys:
HKLMSOFTWAREWOW6432NodeMicrosoftWindows NTCurrentVersionWinlogon
HKCUSoftwareMicrosoftWindowsCurrentVersionExplorerAdvanced (possibly for hidinging files or modifying the file explorer for the logged in user)
HKCUControl PanelScreen Saver.Marquee (Possible for persistance)
HKCRinffileshell (showing instructions for installing a program. Since this is using a .inf file extension, it’ll be using most likely the rundll32.exe to run the file instructions)
In Process Hacker, we can see a lot of the DLLs that’ve unloaded into a “commit” state. Not being mapped in memory yet but will be utilized in this malware sample. Out of these DLLs, the ones that stood out to me the most were bcryptprimitives.dll (which can be an indicator of attempting to compromising the encryption), dbcatq.dll (hijacking of possible DB requests), mswsock (ccreating a connection to another machine),version.dll (checking versions in order to install it’s payload), OnDemandConnRouterHelper.dll and wshom.osx(used for executing these malicious commands).
Here’s a string showing what could be the site of origin. Grabbed from PE Studio:
These handles from to be intresting through the Handles tab on Process Hacker:
- Sessions1BaseNamedObjectswindows_shell_global_counters
- HKLMSOFTWAREWOW6432NodeMicrosoftInternet ExplorerSecurity
Gaara The Kazekage uploaded into some of the tool directories (Ring3 and APIMiner in particular)and any other directory where that I open up in file explorere and prevents usage of these tools hindering analysis:
This self replicating feauture, allows the malware to achieve persistance on it’s target host by copying itself in mutltiple folders. Deleting this file is also not an option because it”ll reappaer about 3 seconds later in the same location.
After viewing this on PE Studio, I can see that these two files are actually the same.
gaara.exe:
Gaara The Kazekage.exe
I opened RegShot and scanned all the directories and found some manipulation with the MS Defender. Parsing through the output file, I found this installed in the Registery:
TsUsbInstaller.dll is also installed in the HKLM hive. Possible usege case could be redirecting the executiong of system funtions via USB.
Intresting…
Fakenet was ran in conjunjction with Wire Shark just to see if these would show any outside connections being made. Also used were Fakenet and InetSim (HTTP simulator) and Fiddler to ensure maximum visibility on any outside connections.
While variations of the network communications tools were running, ProcessHacker was used in tandem and monitored for any child processes that would spwan from the samples. As shown in the image below, Gaara The Kazekage is opened the command prompt breifly and started to use the ping:
Looking into the process’s properties there’s some very unusual functions occuring such as SeChangeNotifyPrevilege. This aids the sample to copy itself to mutliple directories without previlege checks. It’s also operating under an admin account actively if you notice the Use for deny only, (disabled):
Under the general tab, the URL being invoked can be found. It’s pinging using the options -a, for resolving the hostname and -l for declaring the packet size(bytes). The size itself is fairly large for common communication. The 65500 should not be confused with port number as this is a common place to input the port number for recieving or sending information. The large amount could be used for network enumeration to prepare for another stage possibly :
The pings are consistent and appear very frequent (every 20 seconds after detontation).
As of posting this, Virus Total says this has only been flagged by one vendor and it was updated just an hour before writing this:
Once detonated, the sample appaears to have an association under the parent process SearchIndexer.exe, called SearchProtocolHost.exe.
Before:
After:
Under the SearchProtocolHost.exe properties, this command invoked is found under the general tab
“C:Windowssystem32SearchProtocolHost.exe” GlobalUsGthrFltPipeMssGthrPipe3_ GlobalUsGthrCtrlFltPipeMssGthrPipe3 1 -2147483646 “SoftwareMicrosoftWindows Search” “Mozilla/4.0 (compatible; MSIE 6.0; Windows NT; MS Search 4.0 Robot)” “C:ProgramDataMicrosoftSearchDataTempusgthrsvc” “DownLevelDaemon”
This intresting command could be working with the SeChangeNotifyPrevilege and the HKCUControl PanelScreen Saver.Marquee key for maintaining persistance because it searching for background processes.
Admin Previledges
Before executing this sample is admin, Process Hacker is also opened up with admin previldges. When Gaara The Kazekage runs in admin, it actually infects vital Windows background services that are essential for aupporting the OS:
And then executes ping commands from every process:
Process Explorer was also utilized here and ran in admin. But when the Gaara The Kazekage was launched in admin, Process Explorer was killed off.
Further exploring the processes launched, Another domain was discovered:
This seemed to be pinged right after the first domain was dicovered. Once that process was killed off, it ping this host. Unlike in user mode, this domain is only pinged when its run in admin.
End Of Part 1 Analysis:
In conclusion, this is part 1 of 2 from the Gaara The Kazekage analysis report. This analysis describes some persistance mechnismis that are found in here such as the ones found in the registry hives HKCUControl PanelScreen Saver.Marquee , HKUVirtualStoreMACHINESOFTWAREWOW6462NodeGaara-The-Kazekage and it’s ability to copy itself in directories through bypassing previldge checks(SeChangeNotifyPrevilege). This sample is aggressive in that it prevents multiple common tools that are used for analysis. The sample also does have intentions to reach outside the host’s network. Gaara does have more functionality when ran in admin by having control over windows backround services that run in session 0. Enough information is gathered here to understand how the malware functions on a basic level. The next step of the process is to view this in dissassmbly and unpack this.



I want to thank you for your assistance and this post. It’s been great.
Thank you for your articles. I find them very helpful. Could you help me with something?
I’d like to find out more? I’d love to find out more details.
I’d like to find out more? I’d love to find out more details.
Please provide me with more details on the topic
Thanks for sharing excellent informations. Your web site is so cool. I am impressed by the details that you have on this web site. It reveals how nicely you perceive this subject. Bookmarked this website page, will come back for extra articles. You, my friend, ROCK! I found just the info I already searched all over the place and simply couldn’t come across. What a perfect web-site.
I have been examinating out a few of your posts and it’s pretty good stuff. I will surely bookmark your website.
There’s a calm wisdom in your words — like listening to someone who has truly taken the time to understand the world.